[Tool] Eden-RAT——A lightweight Remote Access Tool (RAT) designed for the initial stage of penetration testing
Last Update:
Word Count:
Read Time:
Preface
While developing EgoDrop and DuplexSpy. I successfully implemented an interactive shell within a C#-based GUI application. I then recalled one of my earlier projects that had been suspended due to my limited development experience at the time. Therefore, I decided to revisit and complete it.
The idea of this project originated when I was learning web penetration testing.
When discovering an RCE (Remote Code/Command Execution) vulnerability, we usually demonstrate it with simple Linux commands(e.g., id, whoami, ls, cat /etc/passwd), and that is often the end of the story. However, if we want to conduct further post-exploitation——such as pivoting into the internal network——we may rely on reverse shell tools like metasploit, nc or openssl. Although they are powerful and widely used, they still have certain limitations in practical penetration testing scenario.
Therefore, I decided to develop a GUI-based remote access tool which can be leveraged after achieving RCE, establishing a robust and secure channel with an interactive shell and file manager.
Developing and maintaining this tool entirely on my own is challenging due to limited time, resources, and experience. As a result, the project may still contain undiscovered defects or design flaws. If you encounter any issues while using this tool, please feel free to open an issue or contact me.
If you find this tool informative or helpful, a star ⭐ will be greatly appreciated.
If you are interested in a demonstration of exploitation, please click here.
Introduction
Eden-RAT is a lightweight Remote Access Tool (RAT) designed for the initial stage of penetration testing.
It provides a Graphical User Interface (GUI) with multiple features targeting Linux systems, including a file manager and an interactive shell.
The interactive shell enables full command execution, allowing users to run commands such as ssh, apt, pip install, vim, and other interactive programs seamlessly.
Github Repository: https://github.com/iss4cf0ng/Eden-RAT/
Features
- Eden
- Build Payload
- Multi Listener
- Encrypted Channels
- Infected Machine
- Information
- File Manager
- Display Image
- Edit
- Copy
- Move
- Paste
- Upload
- Download
- Rename
- Datetime
- WGET
- Archive
- Compress
- Extract
- New
- Folder
- Text File
- Process View
- Service View
- Connection
- Disconnect
- Reconnect
Disclaimer
This project was developed out of personal interest in cybersecurity research and education.
It must not be used for illegal or unauthorized activities.
The author is not responsible for any misuse or damage caused by this software.
Getting Started
Eden-RAT consists of three components——Eden-Server, Eden-Client and the payload.
The overall architecture is shown as below:
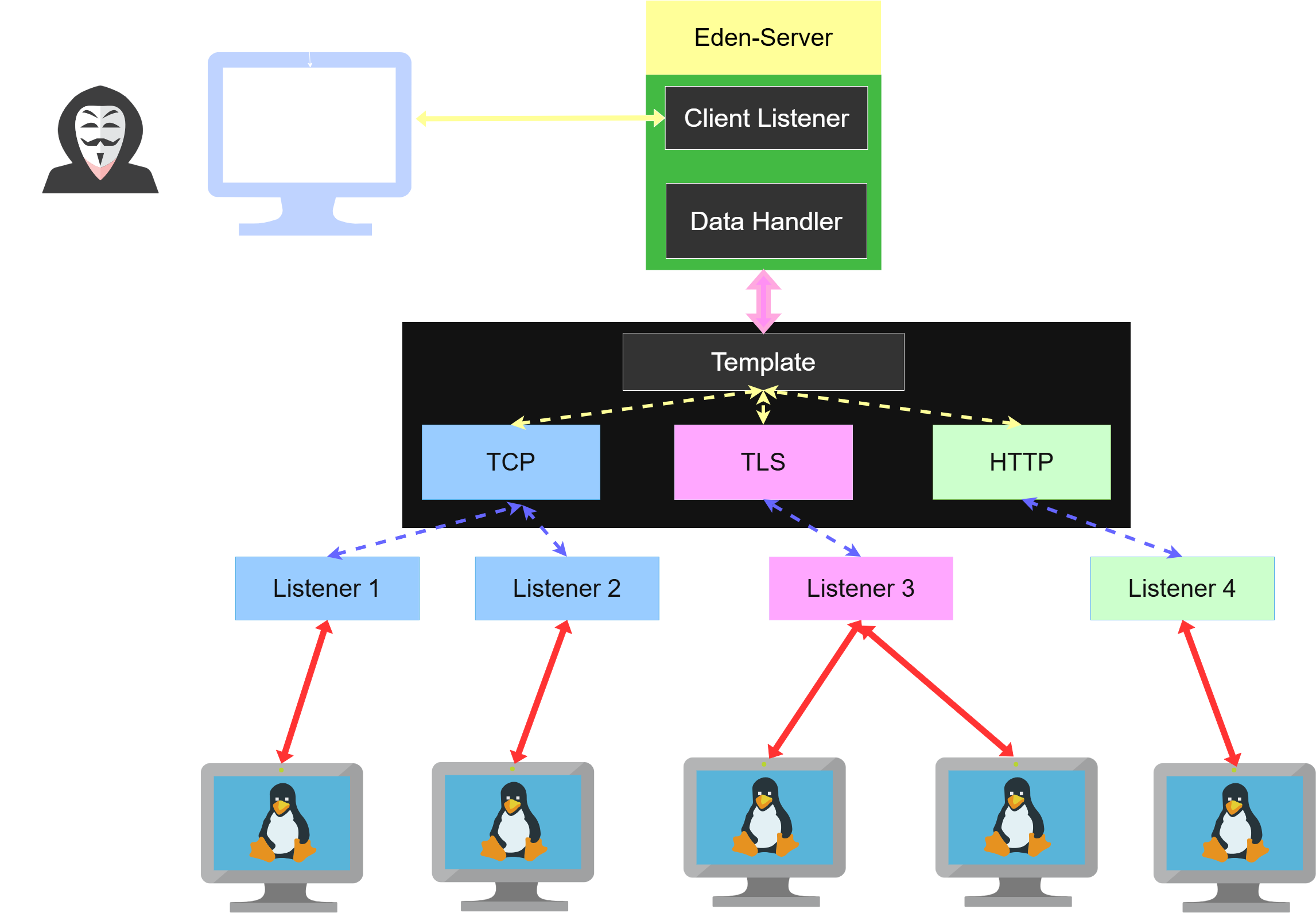
All communication channels are point-to-point encrypted. The communication channel between the Eden-Server and the Eden-Client is encrypted using AES+RSA, while a channel between the Eden-Server and the target Linux server is encrypted using either AES+RSA or TLS.
Eden-Server
An Eden-Server is a python-based socket server. It provides multiple listeners for accepting and handling socket session from Eden-Clients and target Linux servers. It forwards messages between infected Linux systems and Eden-Clients, and processes tasks such as adding listener, building payload requested by Eden-Clients.
Note that an Eden-Server requires pycryptodome.
Available argument:
Eden-Client
An Eden-Client is a C2 user who performs exploitation. All the tasks can only be processed after the Eden-Client connects to an Eden-Server.
Payload
A payload is a script which is used for exploitation. All cryptographic algorithms implemented in the payload are written natively. It means the target Linux server doesn’t requires any third-party libraries (such as pycryptodome), but only a compatible runtime environment (e.g., python 3.10).
Usage
Information
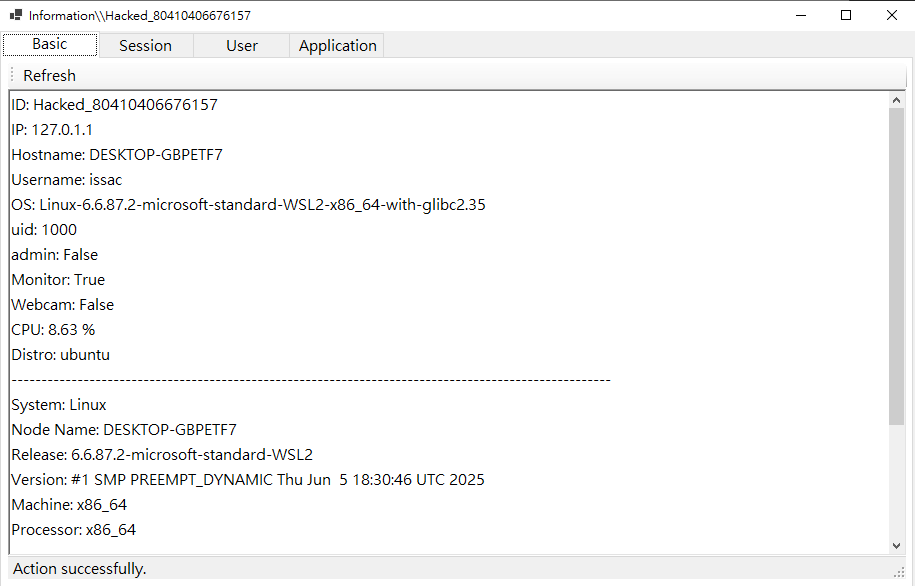
File Manager
Shell
Process View
Service View
Demonstration
Deploy Eden C2 Server
Before starting the C2 server, you need to install pycryptodome:1
pip3 install pycryptodome
After installing the package, you must generate an SSL private key and certificate::1
openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodes
Make sure the files are named exactly:
key.pemcert.pem
Finally, start the C2 server:1
python3 eden_server.py -lvvp 4444
Our Eden-Server has been deployed.

Start Eden Client and Connect to the C2 Server
The default C2 user’s credential are:1
2username = sdksdk
password = 123456
After logging in successfully, you should see the following message box:
Add/Delete a C2 User
1 | |
Note that your input of password is invisible, which is expected.
Generate a payload
Both the encryption and decryption mechanisms are implemented natively (pure implementation).
This means the target platform does not require any third-party libraries.
Infection
You can run the payload script directly:1
python3 payload.py
You can also execute the payload after achieving RCE. If you are interested in a demonstration of exploitation, please click here.
THANKS FOR READING