[DuplexSpy] SOCKS5 Proxy
Last Update:
Word Count:
Read Time:
Introduction
This article demonstrates how to use the proxy feature of DuplexSpy.
This feature allows you to use a compromised machine as a proxy, meaning that all network traffic from your machine can be forwarded through the compromised host.
Even if a compromised machine does not store sensitive data, it can still be abused as a proxy or relay node for malicious activities, such as forwarding SSH sessions. This allows threat actors to hide their real origin and reduce the risk of attribution.
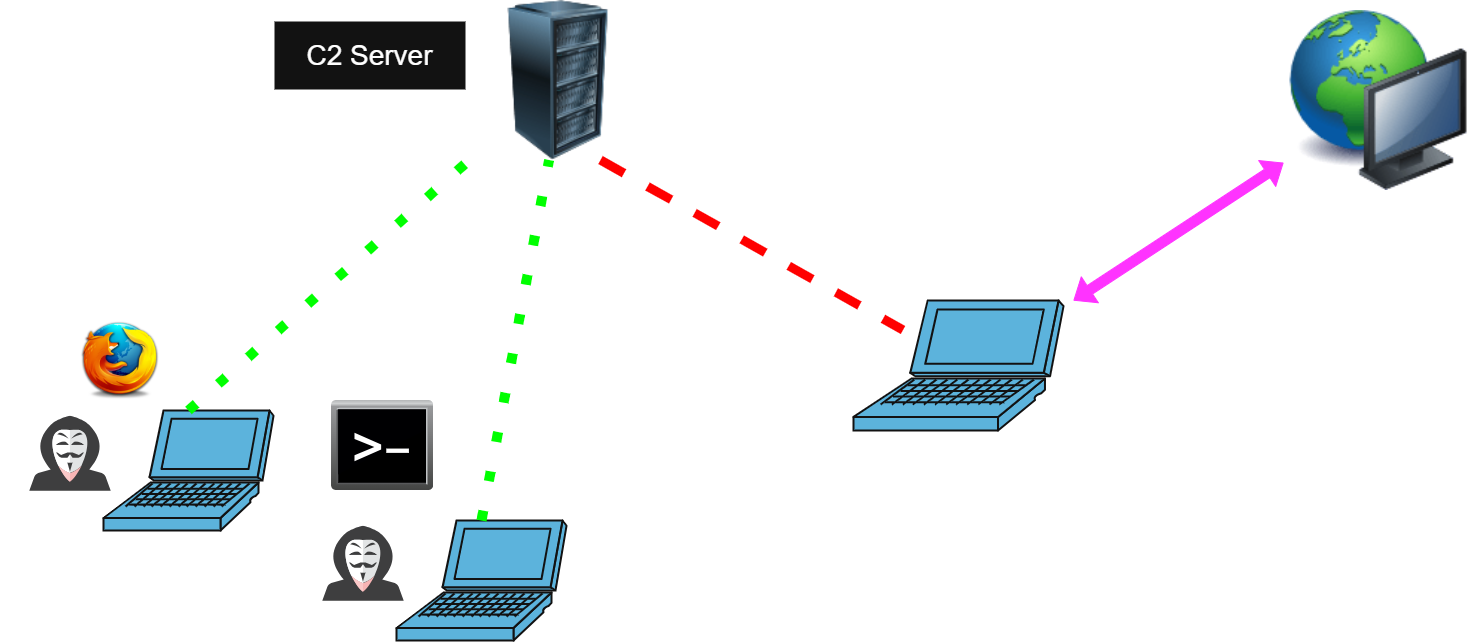
Principle
A C2 server starts listening on one or more ports and accepts SOCKS5 connections from proxy users. The C2 server redirects the user’s network stream to a compromised machine, which then forwards the traffic to the target host. All DNS resolution is performed on the compromised machine.
Usage
In this example, I demonstrates the proxy feature through SSH and proxychains. The following table describes the experimental environment:
| Host | OS | Description |
|---|---|---|
| 10.98.225.138 | Ubuntu VM | Target host. It has enabled SSH service. An important file is stored at ~/Desktop/foo.txt. |
| 10.98.222.136 | Windows 10 x64 | Compromised machine. |
| 10.98.241.11 | Debian Kali Linux | Attacker machine. |
| 10.98.253.150 | Windows 10 | Attacker’s C2 server. |
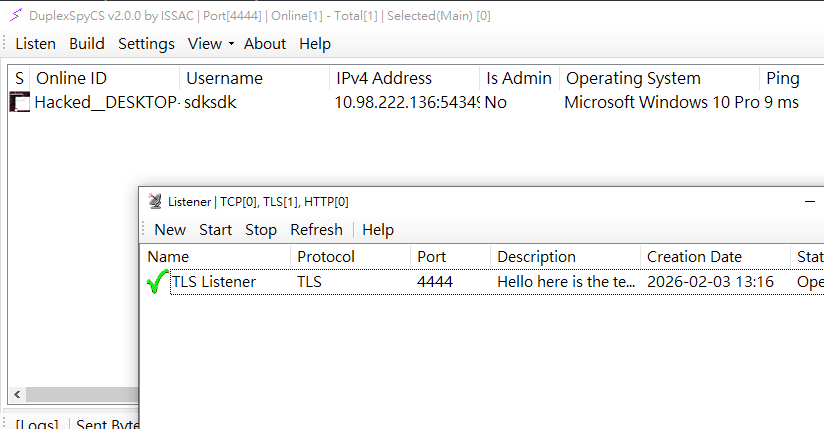
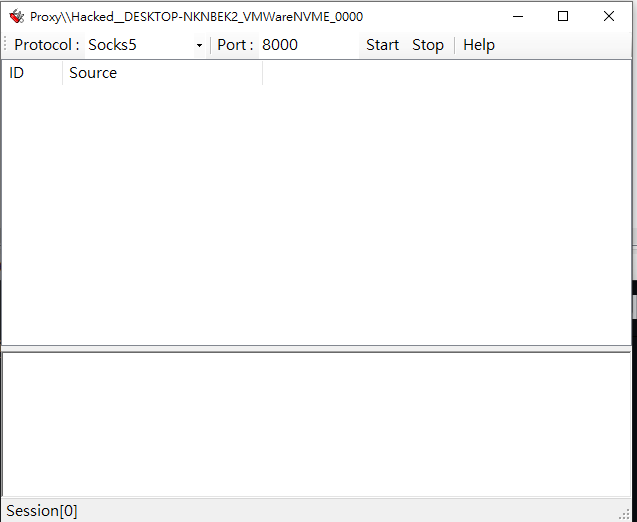
Start the DuplexSpy C2 server:
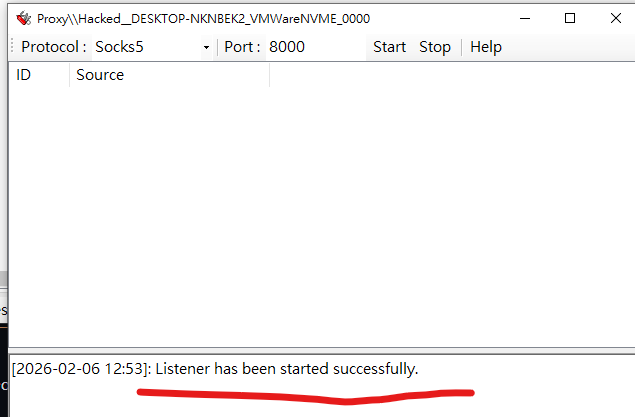
Next, establish an SSH connection from Kali Linux to the target host 10.98.225.138.
Configure the proxychains:1
$ vim /etc/proxychains.conf
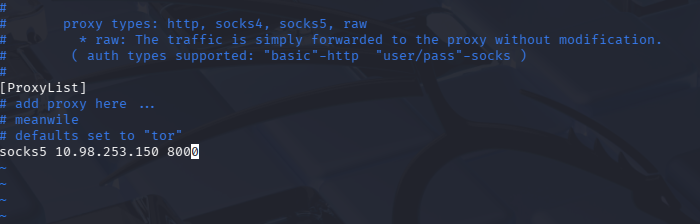
1 | |
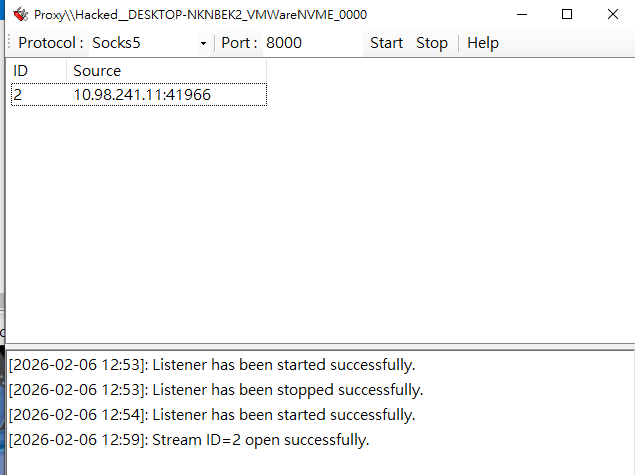
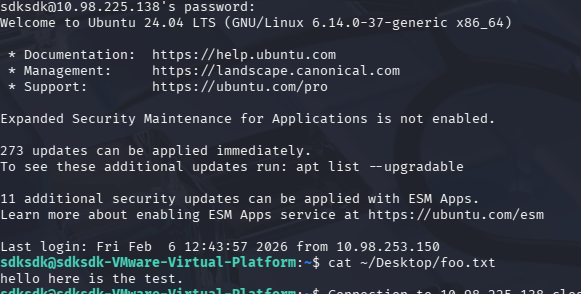
Now, check the source IP address on the target host:1
netstat -ano | grep ":22"
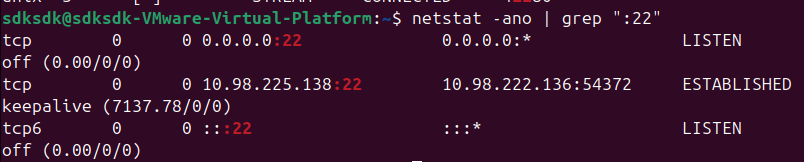
The source address is 10.98.222.136:54372, which belongs to the compromised machine.
THANKS FOR READING!